Tech - Check your Salt - Part 3

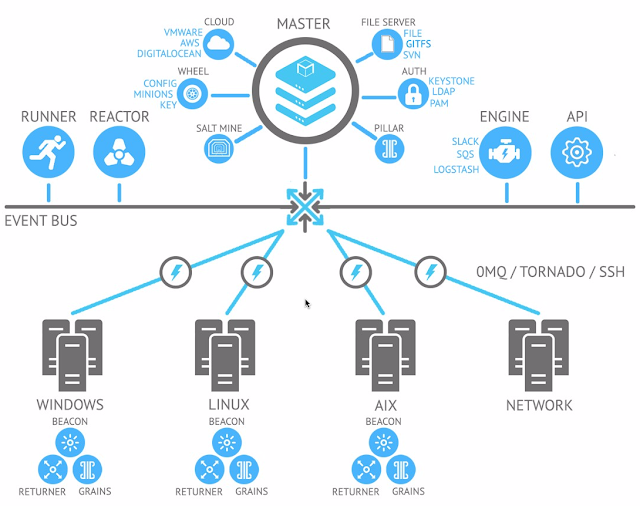
Overview In the previous post , we saw how beacons were deployed in all machines using state files. Salt internally uses zero MQ messaging for communication between the master and minions. As with any messaging framework, there are publisher(s) and consumer(s). One can think of the beacons (on salt minions) as publishers and reactors (on salt master) as consumers. Salt Concepts Covered In this post, the following Salt concepts are covered - Beacons - Monitor minions for state changes, system diagnostics etc. Reactors - Trigger reactions when events occur in the managed systems running minions. Beacons A beacon on the minion can be used to monitor various system events such as - memory usage, CPU load average, overall statistics, user commands etc. The beacon deployed in the previous post contains the 'sh' module. Sh module monitors all commands run on a machine which has the salt minion running. Note: Every time a beacon is deployed to the salt minions,